Setting up Siren Investigate
This section includes information on how to set up Siren Investigate and get it running, including:
-
Supported platforms and version compatibility
-
Installing
-
Configuring
-
Upgrading
|
The instructions in this section are relevant for production deployments only. For a quick trial of Siren, download the Easy Start version and follow the instructions in the README file. |
Supported platforms
Packages of Siren Investigate are provided for and tested with Windows, Linux, and macOS operating systems.
|
Because Siren Investigate runs on Node.js, the required Node.js binaries for these platforms are included. Running Siren Investigate against a separately maintained version of Node.js is not supported. |
Siren Platform is supported on the following Web browsers:
-
Google Chrome
-
Mozilla Firefox
Siren Platform version compatibility
Each Siren Investigate version supports different Elasticsearch/Siren Federate versions in the following way:
-
Minimum supported version: Includes the set of features that are compatible with the Elasticsearch/Siren Federate version that is used.
-
Feature complete version: Includes all of the current Siren Investigate features.
-
Target version: Includes all of the current Siren Investigate features and, being the most up-to-date version, is recommended in most cases.
Version compatibility matrix
|
APIs are at risk of breaking if your Elasticsearch or Siren Federate back-end system is a more recent release than the Siren Investigate version. To reduce this risk, ensure that the difference is limited to only a minor release from the target version; that is, the second number in the sequence <major_release>.<minor_release>.<patch_release>. |
| Siren Investigate | Siren Federate | Elasticsearch |
|---|---|---|
14.4 |
Target: 8.15.5-37.1 |
8.15.5 |
14.3 |
Target: 8.13.4-35.1 |
8.13.4 |
14.2 |
Target: 8.13.2-35.0 |
8.13.2 |
14.1 |
Target: 8.8.2-32.0 |
8.8.2 |
14.0 |
Target: 8.8.2-32.0 |
8.8.2 |
13.5 |
Target: 8.8.2-32.0 |
8.8.2 |
13.4 |
Target: 8.8.2-32.0 |
8.8.2 |
13.3 |
Target: 8.8.2-32.0 |
8.8.2 |
|
When using Elasticsearch 8 or later, you must use xpack security to secure your installation. Searchguard security is supported only in Elasticsearch version 7.x or earlier. |
Installing Siren Investigate
Siren Investigate is provided in the following package formats:
|
The |
|
Siren Investigate Docker images are available at the sirensolutions Dockerhub page. |
|
You can also install the product as a Windows or Linux service. |
Prerequisites
Ensure that you have obtained a license for Siren Platform on the Siren Trial Page.
On Windows, you must install a modern ZIP manager such as 7-zip to extract the platform archives: Windows' built-in ZIP support cannot process the large number of files in the package.
Installing Siren Investigate with the ZIP package
Siren Investigate is provided for Windows, Linux, and macOS as a .zip package. These packages are the easiest formats to use when you are trying Siren Investigate for the first time.
The latest version of Siren Investigate can be found on the Siren Download Page. Descriptions of the separate demonstration packages are also available.
Installing on Linux or macOS
You can download the Linux or macOS (Darwin) .zip packages from the Siren Download Page.
Save the compressed file and extract it to a local directory.
|
If you are running macOS Catalina or a later version, you must remove an extended file attribute (xattr) before you extract the downloaded ZIP file. Run the following command: |
Running Siren Investigate from the Terminal
Start Siren Investigate by opening a Terminal window and running the following command:
./bin/investigateBy default, Siren Investigate runs in the foreground, prints its logs to
STDOUT, and can be stopped by pressing Ctrl + C. The installation is complete when you see the message “[plugin:graph_browser_vis] Status changed from yellow to green - Initialized” in the log window.
After the installation is complete, open a Web browser and navigate to http://localhost:5606.
Folder layout of the ZIP archive
The .zip packages are entirely self-contained. This is very convenient because you do not have to create any directories to start using Siren Investigate, and uninstalling is as easy as removing the folder.
However, it is advisable to change the default locations of the configuration and data folders so that you do not remove important data later on.
| Type | Description | Default Location |
|---|---|---|
home |
Siren Investigate home folder or |
Folder
created by unpacking the archive; in demonstration distributions, the
folder is |
bin |
Binary scripts including |
|
config |
Configuration files including |
|
data |
The location of the data files written to disk by Siren Investigate and its plugins |
|
optimize |
Transpiled source code. Certain administrative actions, for
example |
|
plugins |
The location of the plugin files. Each plugin will be contained in a subfolder. |
|
Installing Siren Investigate on Windows
Download the Windows .zip package from the Siren Download Page.
Save the compressed file and extract it to a local directory.
Running Siren Investigate from the command prompt
Start Siren Investigate by opening a command prompt and running the following command:
.\bin\start.batYou can also run the installation by simply double-clicking on the start.bat file.
By default, Siren Investigate runs in the foreground, prints its logs to
STDOUT, and can be stopped by pressing Ctrl + C. The installation is complete when you see the message “[plugin:graph_browser_vis] Status changed from yellow to green - Initialized” in the log window.
After the installation is complete, open a Web browser and navigate to http://localhost:5606.
Folder layout of Windows ZIP archive
The .zip package is entirely self-contained.
This is very convenient because you do not have to create any directories to start using Siren Investigate, and uninstalling Siren Investigate is as easy as removing the folder. However, it is advisable to change the default locations of the configuration and data folders so that you do not remove important data later on.
| Type | Description | Default Location |
|---|---|---|
home |
Siren Investigate home folder or |
Folder
created by unpacking the archive; in demonstration distributions, the
folder is |
bin |
Binary scripts including |
|
config |
Configuration files including |
|
data |
The location of the data files written to disk by Siren Investigate and its plugins |
|
optimize |
Transpiled source code. Certain administrative actions, for
example |
|
plugins |
The location of the plugin files. Each plugin will be contained in a subfolder. |
|
Running Siren Investigate on Docker
Docker images for Siren Investigate are available from the sirensolutions organization on Dockerhub.
Pulling the Image
Obtaining Siren Investigate for Docker is as simple as issuing a docker pull command.
Option 1: To retrieve the Docker image for the latest version of Siren Investigate, run the following command:
docker pull sirensolutions/siren-platform:latest
docker run -d -p 5606:5606 -p 9220:9220 sirensolutions/siren-platform:latestOption 2: To retrieve a specific version of Siren Investigate, such as version 10.0.0, run the following command:
docker pull sirensolutions/siren-platform:10.0.0
docker run -d -p 5606:5606 -p 9220:9220 sirensolutions/siren-platform:10.0.0Option 3: To retrieve an image that is pre-populated with demonstration data, run the following command:
docker pull sirensolutions/siren-platform-demo-data:latest
docker run -d -p 5606:5606 -p 9220:9220 sirensolutions/siren-platform-demo-data:latestEnvironment variable configuration
Under Docker, Siren Investigate can be configured by using environment variables. When the container starts, a helper process checks the environment for variables that can be mapped to Siren Investigate command-line arguments.
For compatibility with container orchestration systems, these environment variables are written in all capitals, with underscores as word separators. The helper translates these names to valid Siren Investigate setting names.
Some example translations are provided as follows:
Environment Variable |
Siren Investigate Setting |
|
|
|
|
|
|
In general, any setting listed in Configuring Siren Investigate can be configured with this technique.
These variables can be set by using docker-compose as follows:
services:
investigate:
image: sirensolutions/siren-investigate:latest
environment:
SERVER_NAME: siren.example.org
ELASTICSEARCH_URL: http://elasticsearch.example.orgBecause environment variables are translated to CLI arguments, they take
precedence over settings that are configured in the investigate.yml file.
Upgrading Siren Investigate
|
Before you upgrade Siren Investigate, read the breaking changes section of the release notes to learn about the potential effects of upgrading. |
This version of Siren Investigate only supports upgrading from versions 13.2.0 or later. If you need to upgrade from an older version, upgrade to 13.2.0 first before upgrading to this version.
To upgrade Siren Investigate, follow these steps:
-
Save a copy of the Siren Investigate configuration file:
config/investigate.yml. -
Save a copy of any certificate or key that is referenced by
config/investigate.yml; by convention, these files are stored in a directory namedpki. -
Create a back-up of the saved objects index or mappings (for example,
.siren) and the security index or mappings (for example,.sirenaccess) by running the following command:bin/investigate backup --backup-dir=DIR -
In the new version of Siren Investigate, overwrite the
investigate.ymlfile in theconfigfolder with the one that you saved in step 1. -
Restore the files or directories that you saved in step 2 by copying them to the same relative locations in the new installation directory.
-
In the
/pluginsfolder, install the compatible versions of any third-party Siren Investigate plug-ins that you need. -
Run the following upgrade command:
bin/investigate upgrade
|
To see the options that you can use with the backup script, enter the command |
Restoring saved object and security indices
It is possible to restore the indices from a previous backup. See below for a description of the structure and legacy backup types.
|
To see the options that you can use with the restore script, enter the command |
Structure type backups
If the backup was created after version 12.0.0, it will be a structure type which has the following prefixes:
Prefix |
Opening |
|
Saved object data file |
|
Saved object mapping file |
|
Security index mapping file |
|
Security index data file |
The name of the saved object index or the security index in the file is not used. Instead, the structure type restores to the saved object index and security index that are specified in config/investigate.yml.
If the indices are not explicitly specified in the investigate.yml file, .siren and .sirenaccess will be the default saved object index and security index.
Legacy type backups
If the backup was created before version 12.0.0, the legacy type backup restores to the saved object index and security index that are specified in the backup files. Ensure that the files are named as follows:
Prefix |
Opening |
|
Saved object data file |
|
Saved object mapping file |
|
Security index mapping file |
|
Security index data file |
saved-object-index: The value of kibana.index in the config/investigate.yml file when the backup was created. Defaults to .siren.
security-index: The value of investigate_access_control.acl.index when the backup was created. Defaults to .sirenaccess.
Configuring Siren Investigate
The Siren Investigate server reads properties from the
investigate.yml file on startup. The default settings configure
Siren Investigate to run on localhost:5606. To change the host or
port number, or connect to Elasticsearch running on a different machine,
you must update your investigate.yml file. You can also enable SSL
and set a variety of other options.
External datasource configuration is documented in Working with JDBC datasources and access control configuration is documented in Search Guard Classic integration and Siren Investigate access control.
Environment Variable Placeholders
It is possible to use environment variable placeholders in configuration
settings. The syntax of placeholders is ${ENV_VARIABLE_NAME}.
For example, to set elasticsearch.url to the value of the
environment variable ES_URL, edit config/investigate.yml as
follows:
elasticsearch.url: ${ES_URL}| Setting | Description |
|---|---|
|
Default: |
|
Default: |
|
Enables you to specify a path to mount Siren
Investigate as if you are running behind a proxy. This only affects the
URLs generated by Siren Investigate, your proxy is expected to remove
the basePath value before forwarding requests to Siren Investigate. This
setting cannot end in a slash ( |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Specifies directories and role based access rules on the server that will be accessible while importing data from server. |
|
Specifies the server’s directory name. It must be an absolute path to a directory. |
|
Refers to the server’s directory name, it must be unique. |
|
User roles that have access to the server’s directory. Put '*' to allow access for everybody. |
|
Defines which file extensions are allowed for this server’s directory. Supported extensions: .csv, .tsv, .xlsx, .xlsm |
|
Default: |
|
Default: |
|
Number of worker process used to parallelize a data model import files. |
|
Default: |
|
Default: |
|
Default: |
|
The tilemap is the base layer the map visualizations. To increase max zoom level for mapping visualizations, copy the following object in the `investigate.yml`file, this will increase the zoom level to 19 from the default of 15. |
|
The URL to the tile service that Siren Investigate uses to display map tiles in tilemap visualizations. By default, Siren Investigate reads this URL from an external metadata service, but users can still override this parameter to use their own Tile Map Service. |
|
Default: |
|
Default: |
|
Default:
|
|
An array of subdomains used by the
tile service. Specify the position of the subdomain in the URL with the
token |
|
Specifies additional vector layers for use in Region Map visualizations. Each layer object points to an external vector file that contains a GeoJSON FeatureCollection. The file must use the WGS84 coordinate reference system and only include polygons. If the file is hosted on a separate domain from Siren Investigate, the server needs to be CORS (Cross Origin Request Security) enabled so that Siren Investigate can download the file. The following example shows a valid regionmap configuration. It is possible to serve files required by regionmap visualizations from a local folder.
To serve files on a local URL, use the |
|
Mandatory. A description of the map being provided. |
|
Mandatory. The location of the GeoJSON file as provided by a web server. |
|
Optional. References the originating source of the GeoJSON file. |
|
Mandatory. Each layer can contain multiple fields to indicate what properties from the geojson features you want to expose. This example shows how to define multiple properties. |
|
Mandatory. This value is used to do
an inner-join between the document stored in Elasticsearch and the
GeoJSON file. For example, if the field in the GeoJSON is called
|
|
Mandatory. The human readable text that is shown under the Options tab when building the Region Map visualization. |
|
If your Elasticsearch is protected with basic authentication, these settings provide the username and password that the Siren Investigate server uses to perform maintenance on the Siren Investigate index at startup. Your Siren Investigate users still need to authenticate with Elasticsearch, which is proxied through the Siren Investigate server. |
|
Default: For example, a |
|
Default: |
|
Paths to the PEM-format SSL certificate and SSL key files, respectively. |
|
The passphrase that will be used to decrypt the private key. This value is optional as the key may not be encrypted. |
|
List of paths to PEM encoded certificate files that should be trusted. |
|
Default:
|
|
Default:
For more information on the format, and valid options, refer to the OpenSSL cipher list format documentation (https://www.openssl.org/docs/man1.0.2/apps/ciphers.html#CIPHER-LIST-FORMAT). |
|
Optional settings that provide the paths to the PEM-format SSL
certificate and key files. These files are used to verify the identity
of Siren Investigate to Elasticsearch and are required when
|
|
The passphrase that will be used to decrypt the private key. This value is optional as the key may not be encrypted. |
|
Optional setting that enables you to specify a list of paths to the PEM file for the certificate authority for your Elasticsearch instance. |
|
Default: |
|
Default: the value of the
|
|
Default: |
|
Default:
|
|
Default: |
|
Default: |
|
Default: |
|
Specifies the path where Siren Investigate creates the process ID file. |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Default: |
|
Override for cgroup cpu path when
mounted in manner that is inconsistent with |
|
Override for cgroup cpuacct path
when mounted in manner that is inconsistent with |
|
Default: |
|
Default: |
|
An absolute or relative path to a folder. All files from this folder are served at HOST/ui/private_assets URL. For more information, see Serving private assets. |
|
Default: |
|
Default: |
Configuring Siren Investigate logging
To generate logs in Siren Investigate, you must allow and configure logging in investigate.yml. You can control the verbosity, format, and destination of the logs. By default, logs in Siren Investigate are sent to the standard output stdout.
| Setting | Description |
|---|---|
|
Default: |
|
Default: Set the value of this setting to true to suppress all logging output. |
|
Default: Set the value of this setting to true to suppress all logging output other than error messages. |
|
Default: Set the value of this setting to true to log all events, including system usage information and all requests. |
|
Default: Set the value to true to force logging in JSON format when the destination is set to |
|
Allow to retract sensitive information from logging events.
Cookie and authorization header are retracted by default, this can be disabled by setting value to |
|
Default is |
For information about auditing, see Auditing user sessions.
Accessing Siren Investigate
Siren Investigate is a web application that you access through port 5606. All you need to do is point your web browser at the machine where Siren Investigate is running and specify the port number. For example, http://localhost:5606 or http://example.com:5606.
When you access Siren Investigate, the
Discover
page loads by
default with the default index pattern selected. The time filter is set
to the last 15 minutes and the search query is set to match-all (*).
If you do not see any documents, try setting the time filter to a wider time range. If you still do not see any results, it is possible that you do not have any documents.
Checking Siren Investigate status
You can reach the Siren Investigate server’s status page by navigating
to http://localhost:5606/status. The status page displays information
about the server’s resource usage and lists the installed plugins.
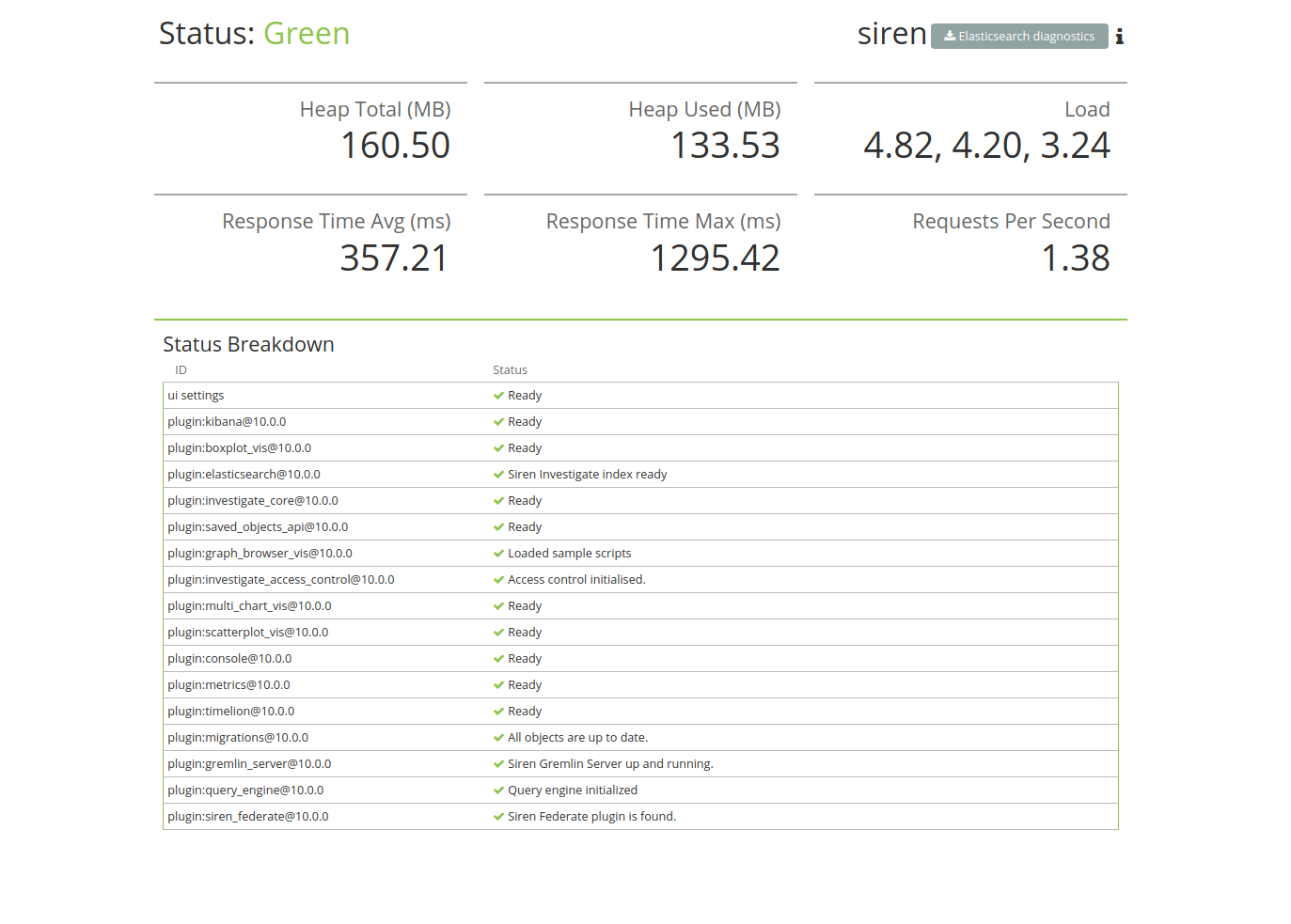
Collecting Elasticsearch diagnostics
Click Elasticsearch diagnostics to generate a single file by collecting different metrics about your Elasticsearch cluster. All collected information are saved to a local file and never transferred over a network. You can see a full list of Elasticsearch API calls by clicking the more info (i) icon.

For JSON formatted server status details, use the API endpoint at
http://localhost:5606/api/status.
|
Connecting Siren Investigate to backend datasources
Siren can visualize data that is accessible by the Siren backend, which is an Elasticsearch cluster enhanced by the Federate plugin.
The following diagram represents this concept. On the frontend, a user looks at data, for example data in a dashboard or on the Graph Link Analysis system. This data comes from Siren "searches", which reflect queries that are sent to indices that are on the Elasticsearch backend.
It is useful to distinguish between two types of searches:
-
Entity tables: Root definitions that describe which Elasticsearch indices will be used. They can be as simple as the name of the index itself or can be “patterns” e.g. new*_ to indicate “all the indices that begin with news_”. For more information and examples, see Entity tables.
-
Other searches: These are defined by filtering an Index Pattern Search, for example starting from a “News” entity table, one might create a “News that contain the word Brexit” search.
Before you can start using Siren Investigate, you need to tell it which Elasticsearch indices you want to explore.
The first time you access Siren Investigate, you are prompted to define an entity_table that matches the name of one or more of your indices. That is all you need to configure to start using Siren Investigate. You can create entity tables at any time from the Management tab.
By default, Siren Investigate connects to the Elasticsearch instance
running on localhost. To connect to a different Elasticsearch
instance, modify the Elasticsearch URL in the investigate.yml
configuration file and restart Siren Investigate. For information about
using Siren Investigate with your production nodes, see
Using Siren Investigate in a production environment
|
-
Point your browser at port 5606 to access the Siren Investigate user interface. For example, http://localhost:5606 or \http://example.com:5606.
-
Specify an pattern that matches the name of one or more of your Elasticsearch indices. You may have to access the data model in the Data Model section. By default, Siren Investigate guesses that you are working with data being fed into Elasticsearch by Logstash. If that’s the case, you can use the default
logstash-*as your entity table. The asterisk (*) matches zero or more characters in an index’s name. If your Elasticsearch indices follow some other naming convention, enter an appropriate pattern. The "pattern" can also be the name of a single index.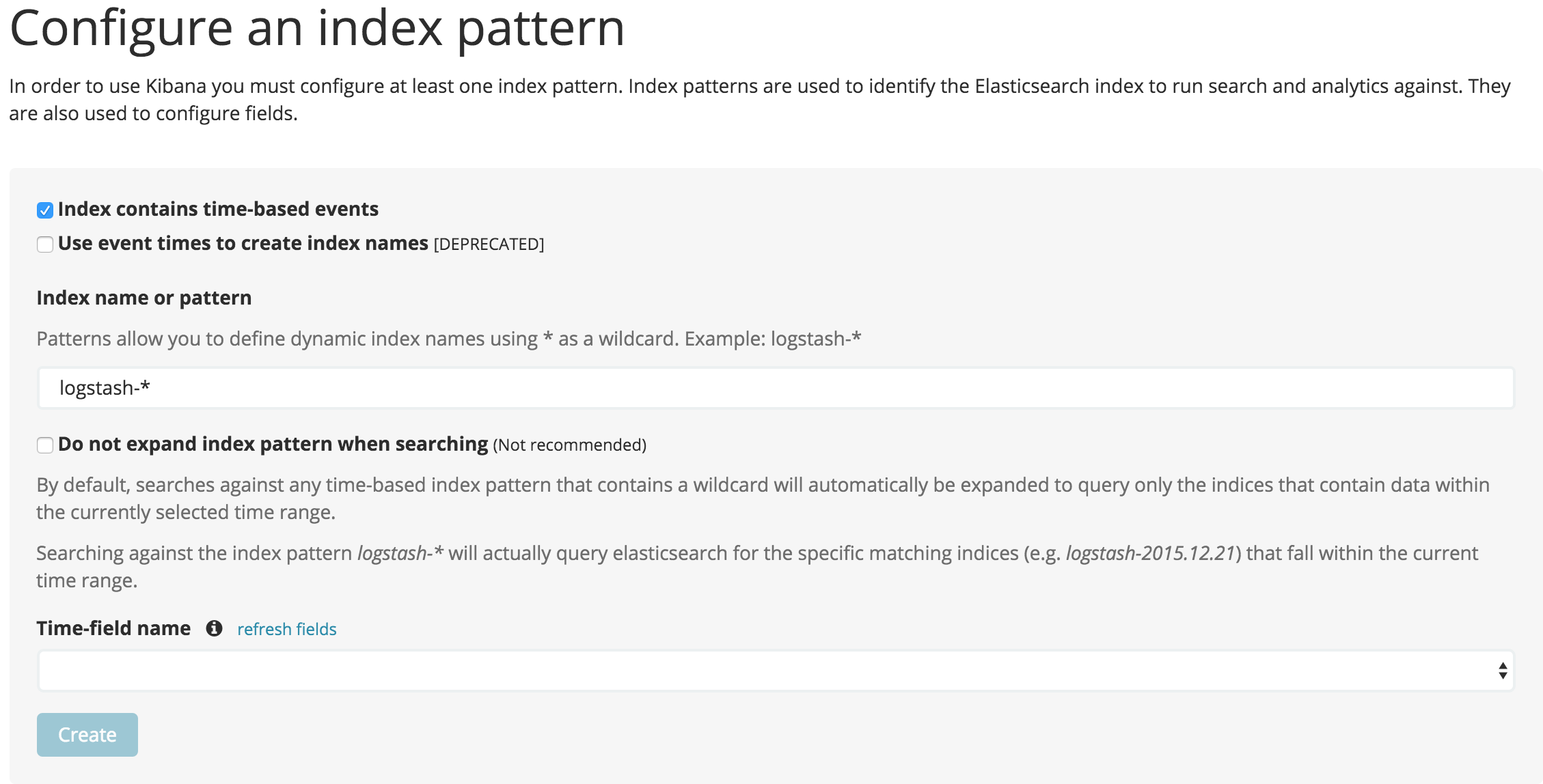
-
Select the index field that contains the timestamp that you want to use to perform time-based comparisons. Siren Investigate reads the index mapping to list all the fields that contain a timestamp. If your index does not have time-based data, switch off the Index contains time-based events option.
-
Click Create to add the entity table.
All done. Siren Investigate is now connected to your Elasticsearch data. Siren Investigate displays a read-only list of fields configured for the matching index.
Siren Investigate relies on dynamic mapping to use fields in
visualizations and manage the .siren index. If you have switched off
dynamic mapping, you need to manually provide mappings for the fields
that Siren Investigate uses to create visualizations. For more
information, see
Siren Investigate and Elasticsearch dynamic mapping
|
Start exploring your data
You are ready to dive in to your data:
-
Search and browse your data interactively from the Discover page.
-
Chart and map your data from the Visualizations page.
-
Create and view custom dashboards from the Dashboard page.
For a step-by-step introduction to these core concepts, see the Easy Start tutorial.
Siren Investigate and Elasticsearch dynamic mapping
By default, Elasticsearch enables
dynamic
mapping for fields. Siren Investigate needs dynamic mapping to use
fields in visualizations correctly, as well as to manage the .siren
index where saved searches, visualizations, and dashboards are stored.
If your Elasticsearch use case requires you to switch off dynamic
mapping, you need to manually provide mappings for fields that Siren
Investigate uses to create visualizations. You also need to manually
enable dynamic mapping for the .siren index.
The following procedure assumes that the .siren index does not
already exist in Elasticsearch and that the index.mapper.dynamic
setting in elasticsearch.yml is set to false:
-
Start Elasticsearch.
-
Create the
.sirenindex with dynamic mapping enabled just for that index:PUT .siren { "index.mapper.dynamic": true } -
Start Siren Investigate and navigate to the web UI and verify that there are no error messages related to dynamic mapping.
Using Siren Investigate in a production environment
How you deploy Siren Investigate largely depends on your use case. If you are the only user, you can run it on your local machine and configure it to point to whatever Elasticsearch instance you want to interact with. Conversely, if you have a large number of heavy users, you may need to load balance across multiple instances that are all connected to the same Elasticsearch cluster.
While Siren Investigate is not terribly resource intensive, we still recommend running Siren Investigate separate from your Elasticsearch data or master nodes.
| Running Siren Investigate in a dedicated node will require at least 5GB of available memory to allow code optimization on initial startup. |
Make sure to set the configuration file as readable only to the user running the Siren Investigate process as it contains encryption keys to protect configuration settings stored in Elasticsearch; if you are connecting Siren Investigate to external datasources, we also recommend to use credentials with no write privileges as they are not required by the system.
Access control
Siren Investigate is compatible with Elastic Stack Security and Search Guard Classic to enable index and document level access control.
For more information about access control features, see the Authentication and access control section.
Configuring a reverse proxy
To protect your system from protocol attacks, it is recommended that you run Siren Investigate behind a reverse proxy.
HTTP servers, such as Apache and NGINX, offer the reverse proxy functionality. See the Enabling HTTPS section for instructions.
Alternatively, you can use a proprietary solution, such as a web application firewall (WAF). Please consult the vendor documentation for instructions.
Load balancing across multiple Elasticsearch nodes
If you have multiple nodes in your Elasticsearch cluster, the easiest way to distribute Siren Investigate requests across the nodes is to run an Elasticsearch client node on the same machine as Siren Investigate. Elasticsearch client nodes are essentially smart load balancers that are part of the cluster. They process incoming HTTP requests, redirect operations to the other nodes in the cluster as needed, and gather and return the results. For more information, see Node in the Elasticsearch reference.
To use a local client node to load balance Siren Investigate requests:
-
Install Elasticsearch on the same machine as Siren Investigate.
-
Configure the node as a client node. In
elasticsearch.yml, set bothnode.dataandnode.mastertofalse:# You want this node to be neither master nor data node, but # to act as a "search load balancer" (fetching data from nodes, # aggregating results, and so on) # node.master: false node.data: false node.ingest: false
-
Configure the client node to join your Elasticsearch cluster. In
elasticsearch.yml, set thecluster.nameto the name of your cluster.cluster.name: "my_cluster"
-
Make sure Siren Investigate is configured to point to your local client node. In
investigate.yml, theelasticsearch.urlshould be set tohttp://localhost:9220.# The Elasticsearch instance to use for all your queries. elasticsearch.url: "http://localhost:9220"