OpenID Connect authentication support
This section offers an overview of how to integrate Siren Investigate with the OpenID Connect authentication support that is provided in the Elastic Stack security Platinum subscription.
Prerequisites
Before you begin, ensure that you have completed the following steps:
-
Configure an OpenID connect realm on your cluster by following the Configure Elasticsearch for OpenID Connect authentication section of the Elasticsearch documentation.
-
Create the roles required by Siren Investigate as explained in the Integrating Elastic Stack security section.
Mapping OpenID Connect roles to Siren Investigate roles
In order to use Siren Investigate with the default configuration you will need to:
-
map at least one OpenID Connect role to the
investigate_adminElasticsearch role; and -
map at least one OpenID Connect role to the
investigate_userElasticsearch role.
To define mappings, refer to the
Mapping users and groups to roles section
of the Elasticsearch documentation. For example, if you want to map an admin OpenID Connect role to
investigate_admin, the following request can be used:
curl -k -XPUT -u elastic https://localhost:9200/_security/role_mapping/investigate_admin -H "Content-Type: application/json" -d '{
"roles": [ "investigate_admin" ],
"enabled": true,
"rules": { "all": [
{ "field": { "realm.name": "oidc1" } },
{ "field": { "groups": "admin" } }
] }
}
'Configuring Siren Investigate
To enable OpenID Connect support in Siren Investigate, you will need to set
the following variables under the investigate_access_control section:
-
public_url: The URL that is used by end users to open Siren Investigate, including the base path. For example, if Siren Investigate is running behind a reverse proxy athttps://investigate.local/investigate, thepublic_urlparameter must be set tohttps://investigate.local/investigate. -
backend: Set the value toxpack. -
backends.xpack.authenticator: Set the value toopenid. -
backends.xpack.openid.realm: The identifier of the OpenID Connect realm, which is declared in the Elasticsearch configuration. For example, given the followingelasticsearch.ymlexcerpt, the value of this option should be set tooidc1:
xpack.security:
enabled: true
authc:
token.enabled: true
realms:
native:
native1:
order: 0
oidc:
oidc1: # the realm identifier
order: 2-
backends.xpack.openid.refresh_interval: If this parameter is set to a number of seconds greater than 0, Siren Investigate will refresh its access token and refresh user information periodically to keep the session alive. If the parameter is not set, the Siren Investigate user session terminates after the access token generated by Elasticsearch expires. The value must be lower than the access token’s lifetime. -
backends.xpack.openid.metadata.display_name: If this parameter is set to a valid OIDC metadata claim reference, Investigate will use the value of the claim as the display name of the user in the sidebar. For example, if your ID token contains afullnameclaim, you can set the parameter tooidc(fullname). Not set by default. OIDC metadata is preserved only in Elasticsearch 7.13.4 and later releases. -
session.backend: By default, Siren Investigate stores user tokens in an encrypted browser cookie. However, this might block the initiation of a session if the tokens are too large to be contained in a 5KB cookie. When you set this option totrue, Siren Investigate stores the tokens in memory and stores only a reference to the session in an encrypted browser cookie. If you are using multiple Siren Investigate instances behind a reverse proxy and the option is enabled, make sure that session affinity is enabled, because the individual Siren Investigate instances do not share back-end sessions between them.
The following is an example of a basic configuration:
investigate_access_control:
enabled: true
public_url: "https://investigate.local/investigate"
acl:
enabled: true
admin_role: investigate_admin
session:
backend: false
cookie:
name: 'kac'
password: '12345678123456781234567812345678'
secure: true
backend: xpack
backends:
xpack:
authenticator: openid
openid:
realm: oidc1
refresh_interval: 60After you apply changes to the investigate_access_control section, restart Siren Investigate.
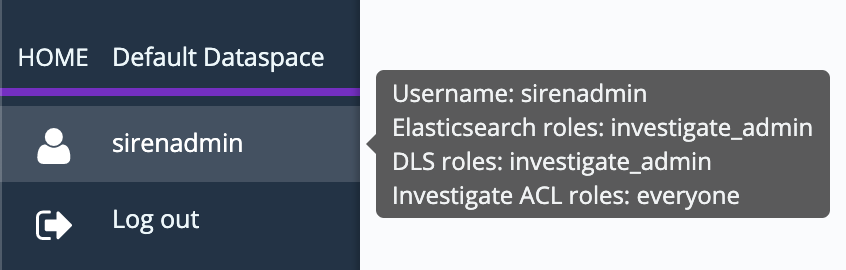
If the configuration is correct, you should be redirected to the Identity Provider login page. After you enter your credentials, you are redirected to Siren Investigate and logged in.
After you are successfully logged in, the user information tooltip lists all of the Elasticsearch roles that are assigned to the user: